Apple may have known for months
Apple stakes a lot of its reputation on how it protects the privacy of its users, as it wants to be the only tech company you trust. But if you send encrypted emails from Apple Mail, there’s currently a way to read some of the text of those emails as if they were unencrypted — and allegedly, Apple’s known about this vulnerability for months without offering a fix.
Before we go any further, you should know this likely only affects a small number of people. You need to be using macOS, Apple Mail, be sending encrypted emails from Apple Mail, not be using FileVault to encrypt your entire system already, and know exactly where in Apple’s system files to be looking for this information. If you were a hacker, you’d need access to those system files, too.
Apple tells The Verge it’s aware of the issue and says it will address it in a future software update. The company also says that only portions of emails are stored. But the fact that Apple is still somehow leaving parts of encrypted emails out in the open, when they’re explicitly supposed to be encrypted, obviously isn’t good.
Only portions of emails are stored
The vulnerability was shared by Bob Gendler, an Apple-focused IT specialist, in a Medium blog published on Wednesday. Gendler says that while trying to figure out how macOS and Siri suggest information to users, he found macOS database files that store information from Mail and other apps which are then used by Siri to better suggest information to users. That isn’t too shocking in and of itself — it makes sense that Apple needs to reference and learn from some of your information to provide you better Siri suggestions.
But Gendler discovered that one of those files, snippets.db, was storing the unencrypted text of emails that were supposed to be encrypted. Here’s an image he shared that’s helpful to explain what’s going on:
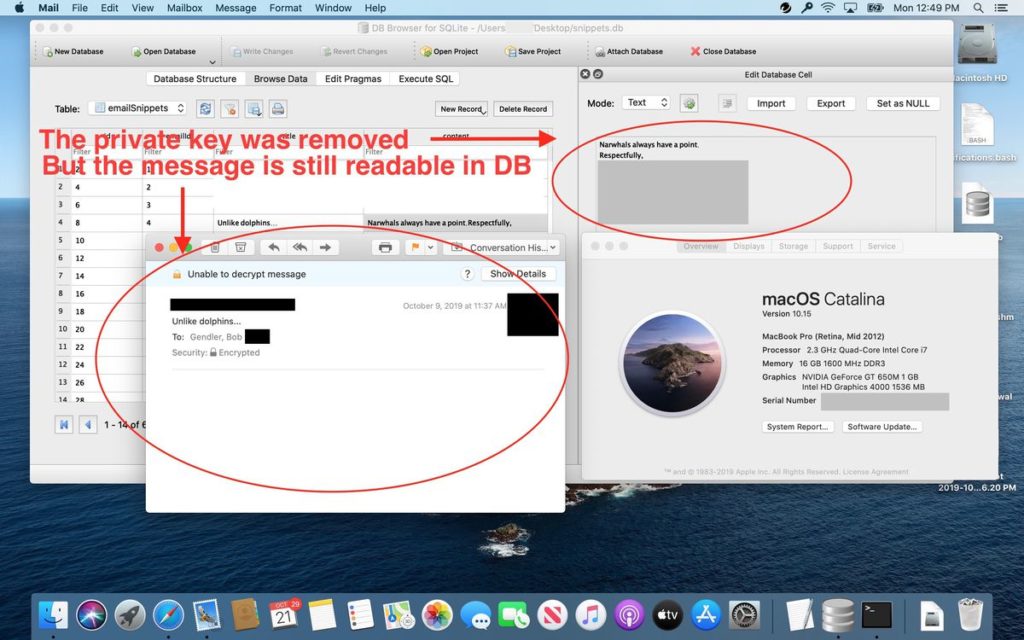
The circle on the left is around an encrypted email, which Gendler’s computer is not able to read, because Gendler says he removed the private key which would typically allow him to do so. But in the circle on the right, you can make out the text of that encrypted email in snippets.db.
Gendler says he tested the four most recent macOS releases — Catalina, Mojave, High Sierra, and Sierra — and could read encrypted email text from snippets.db on all of them. I was able to confirm the existence of snippets.db, and found that it storedportions of some of my emails from Apple Mail. I couldn’t find a way to get snippets.db to store encrypted emails I sent to myself, though.
There’s a way to stop emails from being collected
Gendler first reported the issue to Apple on July 29th, and he says the company didn’t even offer him a temporary solve until November 5th — 99 days later — despite repeated conversations with Apple about the issue. Even though Apple has updated each of the four versions of macOS where Gendler spotted the vulnerability in the months since he reported it, none of those updates contained a true fix.
If you want to stop emails from being collected in snippets.db right now, Apple tells us you can do so by going to System Preferences > Siri > Siri Suggestions & Privacy > Mail and toggling off “Learn from this App.” Apple also provided this solution to Gendler — but he says this temporary solution will only stop new emails from being added to snippets.db. If you want to make sure older emails that may be stored in snippets.db can no longer be scanned, you may need to delete that file, too.
If you want to avoid these unencrypted snippets potentially being read by other apps, you can avoid giving apps full disk access in macOS Catalina, according to Apple — and you probably have very few apps with full disk access. Apple also says that turning on FileVault will encrypt everything on your Mac, if you want to be extra safe.
Again, this vulnerability probably won’t affect that many people. But if you do rely on Apple Mail and believed your Apple Mail emails were 100 percent encrypted, it seems that they’re not. As Gendler says, “It brings up the question of what else is tracked and potentially improperly stored without you realizing it.”












![Hotstar Premium Cookies 2019 [*100% Working & Daily Updated*] Hotstar Premium Cookies 2019 [*100% Working & Daily Updated*]](https://tahav.com/wp-content/uploads/2019/11/Hotstar-Premium-Cookies-Free-100x70.jpg)




Hi, I read your blogs like every week. Your humoristic style is witty, keep it up!