What’s the price of unprotected IT infrastructure? Cybercrime Magazine says that global damages will surpass $6 billion as soon as 2021.
Here we’ll go through some of the most frequent and emerging causes of data breaches in 2019 and see how to address them in a timely manner.
Misconfigured Cloud Storage
It’s hard to find a day without a security incident involving unprotected AWS S3 storage, Elasticsearch, or MongoDB. A global study from Thales and the Ponemon Institute states that only 32% of organizations believe protecting their data in a cloud is their own responsibility. Worse, according to the same report, 51% of the organizations still do not use encryption or tokenization to protect sensitive data in the cloud.
McAfee confirms, claiming that 99% of cloud and IaaS misconfigurations fall into the realm of end users’ control and remain unnoticed. Marco Rottigni, Chief Technical Security Officer EMEA at Qualys, explains the problem: “Some of the most common cloud database implementations ships with no security or access control as standard at the start. They have to be added on deliberately, which can be easily missed.”
With a global average cost of $3.92 million per data breach in 2019, these findings are quite alarming. Sadly, many cybersecurity and IT professionals still candidly believe that cloud providers are responsible for protecting their data in the cloud. Unfortunately, most of their assumptions are not in accord with harsh legal reality.
Virtually all major cloud and IaaS providers have experienced law firms to draft an airtight contract you won’t be able to alter or negate in a court. Black ink clauses expressly shift financial liability for most incidents on the clients’ shoulders and establish limited liability for everything else, often reckoned in pennies.
Most SME companies don’t even carefully read the terms, while in large organizations, they are reviewed by legal advisors who are often disconnected from the IT team. Though, one will hardly negotiate better conditions, as otherwise, cloud business will become so perilous and unprofitable that it will swiftly disappear. This means that you will be the sole entity to blame and punish for misconfigured or abandoned cloud storage and a resultant data breach.
Unprotected Code Repositories
Research by North Carolina State University (NCSU) found that over 100,000 GitHub repositories have been leaking secret API tokens and cryptographic keys, with thousands of new repositories exposing secrets on a daily basis. Canadian banking giant Scotiabank recently made news headlines by reportedly storing internal source code, login credentials, and access keys for months in publicly open and accessible GitHub repositories.
Third-parties, especially external software developers, are commonly the weakest link. Often their developers lack proper training and security awareness requisite to duly safeguard their code. Having several projects at once, tough deadlines, and impatient clients, they ignore or forget about the very fundamentals of security, letting their code in public domain.
Cybercriminals are well aware of this digital Ali Baba’s cave. Cyber gangs specialized in OSINT data discovery meticulously crawl existing and new code repositories in a continuous mode, carefully scrapping the data. Once something of value is found, it’s sold to cyber gangs focused on exploitation and offensive operations to get in.
Given that such intrusions rarely trigger any red flags in anomaly detection systems, they remain unnoticed or detected once it is already too late. Worse, the investigation of such intrusions is costly and almost perspectiveless. Many famous APT attacks involved password re-use attacks with credentials found in code repositories.
Vulnerable Open Source Software
The rapid proliferation of Open Source Software (OSS) in enterprise systems exacerbates the cyber-threat landscape by adding even more unknowns into the game. A recent report by ImmuniWeb found that 97 out of 100 largest banks are vulnerable and have poorly coded web and mobile apps, being riddled with outdated and vulnerable open source components, libraries, and frameworks. The oldest unpatched vulnerability found was known and publicly disclosed since 2011.
OSS does save a lot of time for developers and money for organizations but likewise provides a wide spectrum of concomitant and largely underestimated risks. Few organizations properly track and maintain an inventory of countless OSS and its components built into their enterprise software. Consequently, blinded with unknowingness, they fall victim to unknown unknowns when newly detected OSS security flaws are aggressively exploited in the wild.
Today, medium and large-sized organizations incrementally invest in application security, notably in the implementation of DevSecOps and Shift Left testing. Gartner urges the adoption of Shift Left software testing by incorporating security testing at the early stages of the Software Development Lifecycle (SDLC) before it becomes overly expensive and time-consuming to fix vulnerabilities. However, a holistic and up2date inventory of your OSS is indispensable to implement Shift Left testing; otherwise, you will just pour your money down the drain.
How to Prevent and Remediate
Follow these five recommendations to reduce your risks in a cost-efficient manner:
1. Maintain an up2date and holistic inventory of your digital assets
Software, hardware, data, users, and licenses should be continuously monitored, classified, and risk-scored. In the era of public cloud, containers, code repositories, file-sharing services, and outsourcing, it’s not an easy task, but without it, you may ruin the integrity of your cybersecurity efforts and negate all previous cybersecurity investments. Remember, you cannot protect what you don’t see.
2. Monitor your external attack surface and risk exposure
Many organizations spend money on auxiliary or even theoretical risks, ignoring their numerous outdated, abandoned, or simply unknown systems accessible from the Internet. These shadow assets are low-hanging fruit for cybercriminals. Attackers are smart and pragmatic; they won’t assault your castle if they can silently get in via a forgotten underground tunnel. Therefore, ascertain that you have an ample and up2date view of your external attacks surface in a continuous manner.
3. Keep your software up2date, implement patch management and automated patching
Most of the successful attacks do not involve the usage of sophisticated and costly 0days but publicly disclosed vulnerabilities often available with a working exploit. Hackers will systematically search for the weakest link in your defense perimeter to get in, and even a tiny outdated JS library may be a windfall to get your crown jewels. Implement, test, and monitor a robust patch management system for all your systems and applications.
4. Prioritize your testing and remediation efforts based on risks and threats
Once you have crystal-clear visibility of your digital assets and a properly implemented patch management strategy, it’s time to ensure that everything works as you expected. Deploy continuous security monitoring for all your external assets, conduct in-depth testing, including penetration testing of your business-critical web applications and APIs. Setup monitoring for any anomalies with rapid notifications.
5. Keep an eye on Dark Web and monitor data leaks
Most companies do not realize how many of their corporate accounts, exposed by hacked third-party websites and services, are being sold on the Dark Web. The emerging success of password reuse and brute-force attacks stem from it. Worse, even legitimate websites such as Pastebin often expose a great wealth of leaked, stolen, or lost data accessible to everyone. Continuous monitoring and analysis of these incidents may save millions of dollars and, most importantly, your reputation and goodwill.
Reducing Complexity and Costs
We came across an innovative offering from a Swiss company ImmuniWeb® to tackle these issues in a simple and cost-effective manner. We are truly impressed with its technical capabilities, consolidated approach, and accessible price.
ImmuniWeb Discovery provides you with superior visibility and control over your external attack surface and risk exposure.
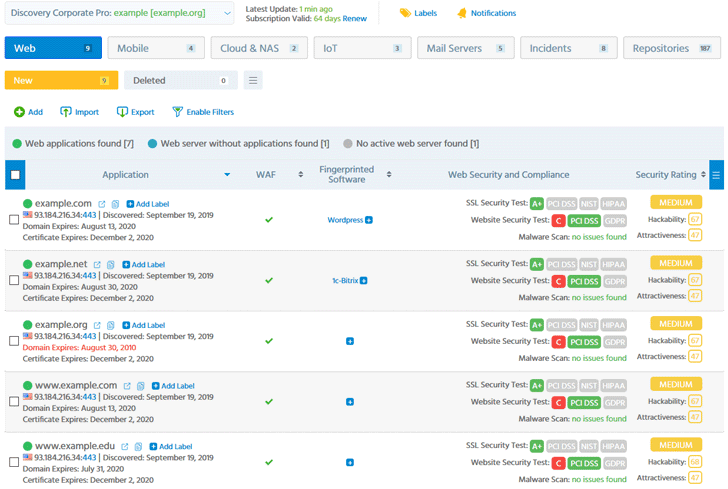
Try ImmuniWeb® Discovery for:
- Rapid discovery of your external digital assets, including APIs, cloud storage and IoT
- Actionable, data-driven security ratings of your applications’ Hackability and Attractiveness
- Continuous monitoring of public code repositories for unprotected or leaked source code
- Continuous monitoring of Dark Web for exposed credentials and other sensitive data
- Production-safe Software Composition Analysis of your web and mobile applications
- Instant alerts about expiring domain names and SSL certificates
- Integration with SIEMs and other security systems via API
We hope you will avoid becoming a victim of a data breach in 2020!











![Hotstar Premium Cookies 2019 [*100% Working & Daily Updated*] Hotstar Premium Cookies 2019 [*100% Working & Daily Updated*]](https://tahav.com/wp-content/uploads/2019/11/Hotstar-Premium-Cookies-Free-100x70.jpg)



