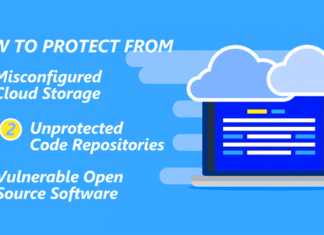
How to Avoid the Top Three Causes of Data Breaches in 2019
What's the price of unprotected IT infrastructure? Cybercrime Magazine says that global damages will surpass $6 billion as soon as 2021.
Here we'll go through some of the most frequent...
How to Hack Facebook Using Phishing
Disclaimer: This article has been written for educational purpose only.We don’t encourage hacking or cracking. In fact we are here discussing the ways that hackers are using to hack our digital assets....
6 Gadgets you should bring home this summer
6 Gadgets you should bring home this summer available on amazon
CHOETECH Portable Waterproof Solar ChargerJBL CLIP 3 Portable Bluetooth SpeakerOrient Electric Aeroslim 1200mm Smart Premium Ceiling FanSamsung Curd...
How to mute a contact on Instagram
Instagram is great to have, but there are times when it gets jarring and you desperately need to ignore certain people, but don't want them to know. Well, just read on to...
How to make your own hand sanitizer
Washing your hands is how you protect yourself, but this is second best
Everyone agrees, including the Centers for Disease Control and Prevention (CDC), that if you want...
How to upgrade to Windows 10 for free
A free upgrade is still available for Windows 7 and Windows 8.1 users
Anyone still using an older version of Windows should figure out how to upgrade to Windows...
YouTube tracking: This is how much Google knows about you; here is how to...
YouTube tracking: Google knows lot about you and if you are on YouTube, check these settings to quickly stop the company in its tracks.
YouTube is the world’s largest...
Step By Step Guide To Unlock And Recover Files From Locked SD Card
SD cards are one of the most widely used data storage solutions, especially for avid photographers who heavily rely on cameras to earn their bread and butter. As someone who also uses...
How to Detect if Someone’s Stealing Your WiFi
Everywhere you go these days, data is whizzing through the airwaves.
While we use 4G and 5G data on our smartphones as we're driving or walking, WiFi still dominates...
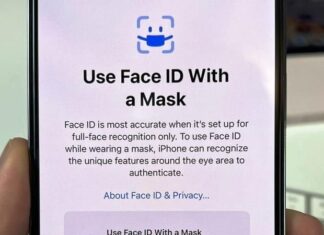
iOS 15.4: How to use Face ID to unlock iPhone while wearing a face...
iPhone owners could soon be able to use Face ID while still wearing their masks.
You have probably used FaceID with a mask to unlock your iPhone, and it’s...
















![Hotstar Premium Cookies 2019 [*100% Working & Daily Updated*] Hotstar Premium Cookies 2019 [*100% Working & Daily Updated*]](https://tahav.com/wp-content/uploads/2019/11/Hotstar-Premium-Cookies-Free-100x70.jpg)

