Threat actors are selling over 267 million Facebook profiles for £500 ($623) on dark web sites and hacker forums. While none of these records include passwords, they do contain information that could allow attackers to perform spear phishing or SMS attacks to steal credentials.
Last month, security researcher Bob Diachenko discovered an open Elasticsearch database that contained a little over 267 million Facebook records, with most being users from the United States.
For many of these records, they contained a user’s full name, their phone number, and a unique Facebook ID.
The ISP hosting the database eventually took the server offline after being contacted by Diachenko.
Soon after, a second server containing the same data plus an addition 42 million records was brought online but was quickly attacked by unknown threat actors who left a message telling the owners to secure their servers.
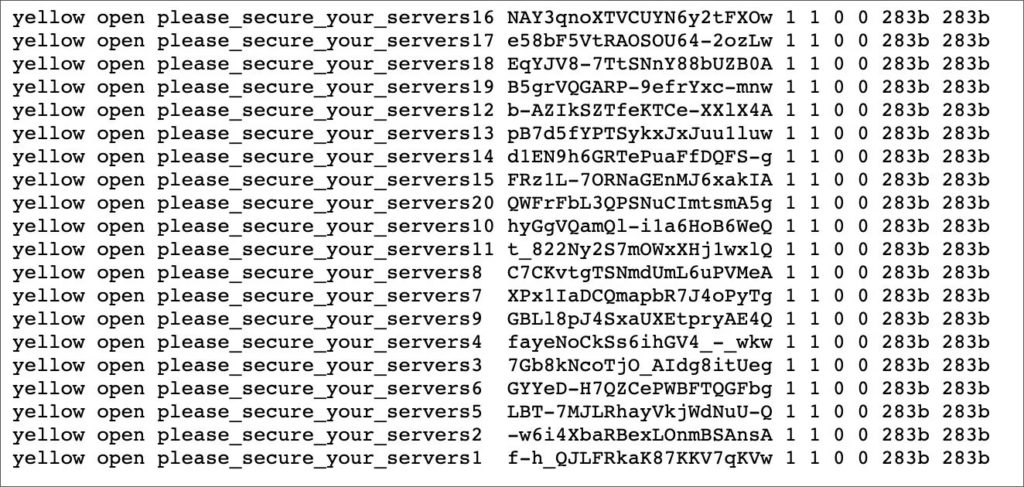
Of this new data, 16.8 million records included more information such as a Facebook user’s email address, birth date, and gender.
It was not discovered who these servers belonged to, but Diachenko believed that it was owned by a criminal organization who stole the data using the Facebook API before it was locked down or via scraping public profiles.
Data now being sold for £500
This weekend, cybersecurity intelligence firm Cyble discovered a threat actor selling this database for £500 on the dark web and through hacking forums.
In a conversation with Beenu Arora, CEO of Cyble, BleepingComputer was told that the researchers have purchased the database to verify the data and that they are adding it to their http://AmIbreached.com breach notification service.
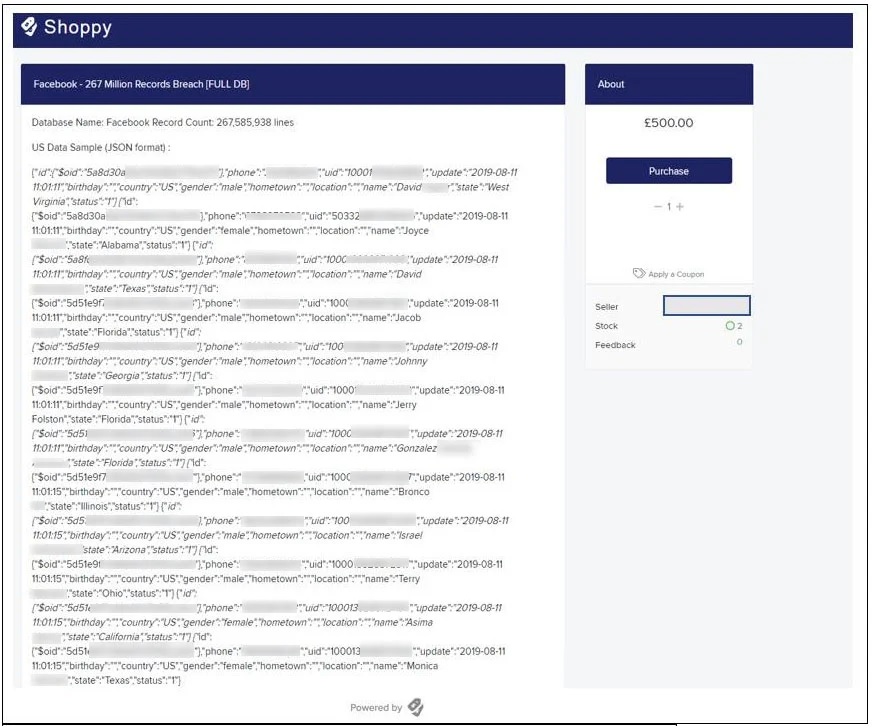
Redacted by BleepingComputer
Like Diachenko, Arora is unsure how this data was compiled.
“At this stage, we are not aware of how the data got leaked at the first instance, it might be due to a leakage in third-party API or scrapping,” Arora told BleepingComputer. “Given the data contain sensitive details on the users, it might be used by cybercriminals for phishing and spamming.”
How can this sold data affect you?
The database being sold does not contain Facebook account passwords, but it does contain email addresses and phone numbers for some users.
This could allow attackers to create spear-phishing campaigns that aim to steal your password using email campaigns or SMS texts that pretend to be from Facebook.
If the phishing emails contain information such as dates of birth and/or phone numbers, some users may be more prone to believe them and thus provide the attackers with the requested info.
Cyble recommends users tighten their privacy settings on Facebook accounts and be cautious of unsolicited emails and text messages.












![Hotstar Premium Cookies 2019 [*100% Working & Daily Updated*] Hotstar Premium Cookies 2019 [*100% Working & Daily Updated*]](https://tahav.com/wp-content/uploads/2019/11/Hotstar-Premium-Cookies-Free-100x70.jpg)



